
It’s all about domains… | Keith Mitchell (DNS-OARC)
The DNS is a critical system that needs everyone's cooperation. As a true internet expert, Keith Mitchell knows this first hand. It is the reason he runs DNS-OARC. We met Keith to discuss how essential the DNS is for what we love most: Domains!
Published by

Simone Catania
Date

The DNS is a fundamental part of the internet. It is a core part of connecting to the internet and providing data to others. Information sharing, operational characterization, workshops, analysis, tools and services are just some of the critical functions offered by DNS-OARC, a project from and for the DNS community that is currently managed by Keith Mitchell, our interview guest today.
With a solid academic background in communications networks and distributed systems, Keith started working on making internet services available in the UK in the late ’80s, eventually working for UK’s first commercial Internet provider in the ’90s. This is just the beginning of a career that has seen him in executive positions in several organizations devoted to the network of networks.
To name just a few, Keith has served as a non-executive Director of Nominet UK (1996-2002) and Chairman of the RIPE NCC Executive Board (1997-99). In 2006, he moved to the US to work at the DNS Operations, Analysis and Research Center (DNS-OARC), a non-for-profit that aims to bring together DNS operators, implementors and researchers so they can coordinate responses to attacks and other concerns, share information and learn together. Let’s meet Keith!

One of the interesting things about the DNS is that it is both a victim and vector for DDoS attacks. At the same time, it is also an essential tool for their detection, measurement and mitigation. Our mission at DNS-OARC is to effectively improve our understanding of the matter to address this problem.
1. You can look back at a successful career in the internet industry. What were your most significant achievements?
Much of my background has been in the early ISP and IXP space, where I founded the UK’s first commercial ISP and the London Internet Exchange, but the DNS industry has always sought a piece of me too.
One of the achievements I look back on with pride is being one of the co-founders of Nominet, the .uk registry. Today, it remains one of the world’s most well-managed, biggest and most innovative registries.
I additionally spent some time at the Internet Systems Consortium (ISC), overseeing the development of BIND and the operation of one of the internet’s root name server instances. Finally, I founded and continue to run the United Kingdom Network Operators’ Forum (UKNOF) to bring together operational, technical and engineering information exchange related to networking technologies and practices.
In recent years, I have focused my energies on a new project: the DNS Operations, Analysis, and Research Center (DNS-OARC). Spinning off DNS-OARC from a half-person project within the ISC to the robust and diverse membership organization it has become over the past 15 years has been a fantastic and rewarding journey.
Isn’t the internet one of the most disruptive inventions of human history? We present to you the organizations that make online communication possible.
2. What is the objective of DNS-OARC, the association you head today?
DNS-OARC aims to improve the DNS by bringing together key players, from operators and researchers to open-source and vendor communities. We focus on facilitating and applying the scientific method to the internet infrastructure. This means we gather, analyze and publish data from the live DNS and collaborate through the open workshops we run. We provide various tools, infrastructure, open-source software, and collaboration platforms to our strong community of members for more comprehensive public benefit.
One of our most popular collaboration platforms is based on a Mattermost open-source chat. We deployed it during the pandemic to help run our workshops and bring the community together while everything was online. However, its uptake has kept increasing since then and we’ve found other interesting uses. For example, in case of incidents concerning the DNS, we’ve used Mattermost to bring together the key people at the affected organizations and have them work together in real-time to address the issues.
We usually run two to three workshops annually and all slides and videos are available on a dedicated online page and our YouTube channel; OARC’s community likes us to co-locate within big internet industry events such as RIPE, NANOG, IETF and ICANN. For example, in October 2022, we ran the OARC39 workshop. It took place in Belgrade, Serbia, and our partners included RNIDS (the .rs ccTLD registry), the local IXP SOX who hosted our meeting and CENTR, all co-located within the RIPE85 meeting. We had over 30 presentations with 120 attendees.
Find perfect domains
3. DNS-OARC makes open-source tools available to the community. What kind of tools are they and how do they support DNS experts?
Today, our tool repository on GitHub for DNS data collection, measurement and analysis contains over 30 projects! We developed some in-house, partially through grant funding. Our members also donated towards some and others have been “adopted” as orphan projects.
OARC’s open-source tools fall into two broad categories. On one side, we develop testing tools for performance, conformance measurement and debugging (e.g. dnsperf, DNZViz, CheckMyDNS). On the other side, we offer statistics and measurement tools for gathering and displaying telemetry on DNS infrastructure, e.g., Domain Statistics Collector (DSC), dnscap (packet capture) and templates for helping display DNS statistics using grafana.
The key thing to understand is that none of these are software that implements or provides DNS service. Instead, they enable you to better understand and manage your DNS infrastructure.
Attackers can manipulate the DNS in several ways and gain big payoffs. But there are ways of protecting yourself and your business. Learn about the most common DNS attack methods and how to protect yourself.
4. What are the most effective DNS security mechanisms today?
DNS security is essential because it can help protect you against the increasing number of vulnerabilities that have cropped up over the years with a system that was not initially developed to be secure.
DNSSEC remains the best way to ensure the end-to-end integrity of DNS data, i.e., you can verify that the answers you are getting are indeed from the site you are accessing and have not been tampered with along the way. While DNSSEC is a powerful and mature technology, it remains challenging to implement and deploy for many. This is why, in partnership with Casey Deccio, Assistant Professor in the Computer Science Department at Brigham Young University (BYU), we host DNSViz, a tool for visualizing and debugging DNSSEC transactions.
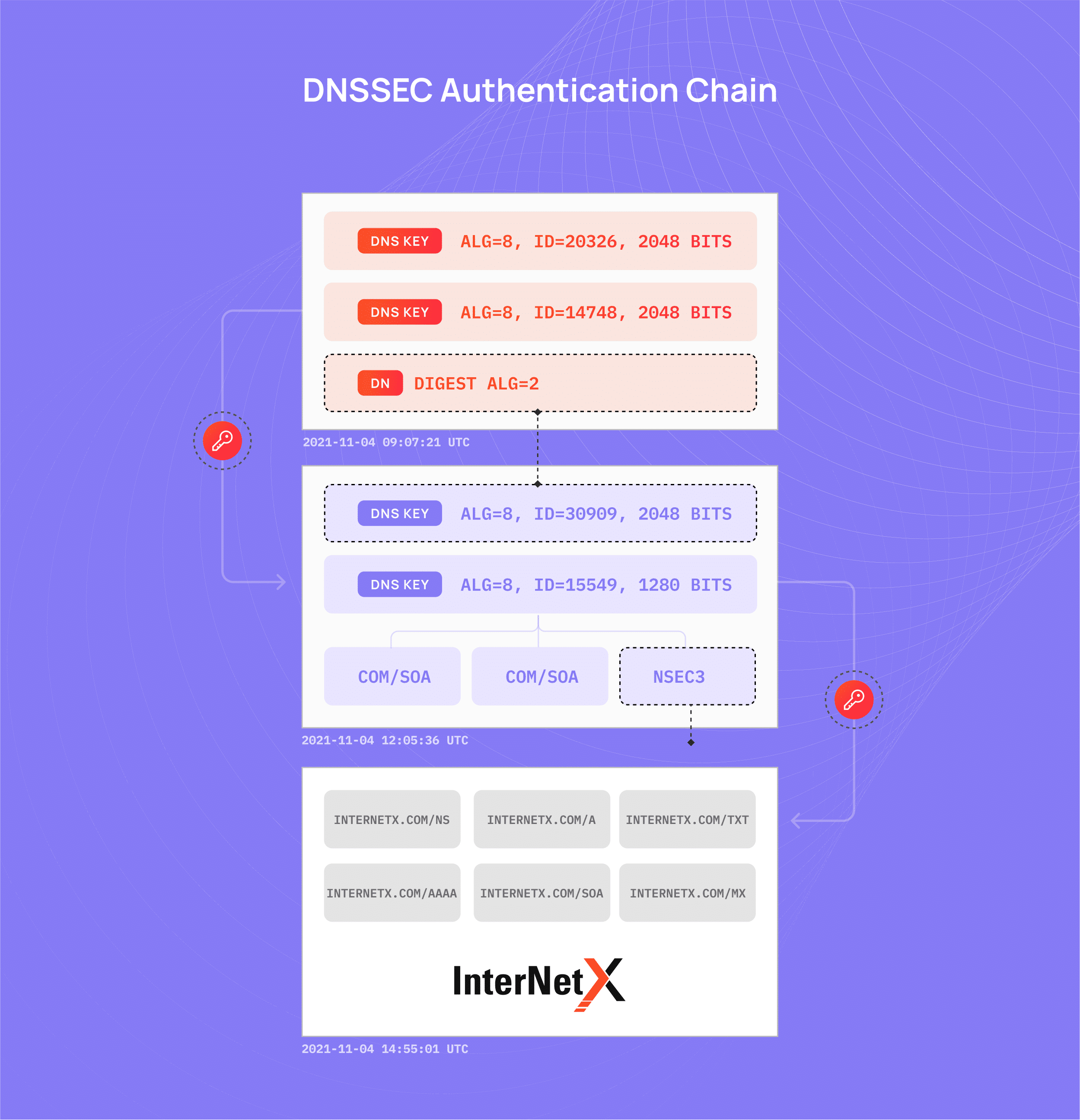
More recent entrants into the DNS security space include technologies for protecting queries and responses between the end-user and their chosen resolver operator via encryption, such as DNS-over-QUIC (DoQ), DNS-over-HTTPS (DoH) and DNS-over-TCP (DoT).
DoQ is a newcomer but is experiencing some traction. We’ve recently added DoQ capability to our CheckMyDNS tester to help people verify that it is working. DoH is getting a lot of support from the browser industry. Mozilla and Comcast recently funded us to add support for this to our dnsperf performance testing tool.
There’s also DNS-over-TCP (DoT), which is perhaps more popular with enterprise and institutional network operators. It helps them ensure security filtering for their user communities, along with encrypted DNS query safety.
5. DoS and DDoS are a real plague for DNS. What are the challenges and possible mitigations available?
One of the interesting things about the DNS is that it is both a victim and vector for DDoS attacks. At the same time, it is also an essential tool for their detection, measurement and mitigation. Our mission at DNS-OARC is to effectively improve our understanding of the matter to address this problem.
The most effective mitigations against DoS and DDoS are:
Anycast
It is the most effective tool in the DNS box against DDoS. Here servers for given zones are hosted at the same IP address in many different places on the internet. The root server operators pioneered this network addressing and routing methodology. When combined with massive over-provisioning, Anycast makes it very difficult for an attack to overwhelm all of the servers for a particular operator or zone.
Response Rate Limiting (RRL)
With this critical tool, servers under excessive load randomly discard traffic from and for particular sources. RRL effectively avoids the servers’ exhaustion under attack and minimizes their ability to cause damage elsewhere.
Source Address Validation (SAV)
Source Address Validation (SAV) is also a practical and effective solution against Dos and DDoS. All ISPs and cloud operators should deploy it only to allow traffic from the networks with the assigned source addresses.
This shouldn’t require as much advocacy as it still does in 2022, but there are still corners of the internet where bad guys can spoof source addresses of the traffic they send to cause amplified replies (including via DNS) back to victims.





